Overveiw
Overveiw
Summary
With the rapid development of mobile terminal industry, mobile devices have brought many security and privacy issues while penetrating people’s lives. Among them, there are three major issues of the security and privacy for existing mobile devices:
- For the high-security mobile devices where all communication methods are disabled, is it secure enough to prevent the confidential data from being leaked?
- Although the mobile device/operating system prevents third-party app developers from accessing system kernel information, are there other ways to infer the app usage behavior of mobile users?
- The proliferation of cameras and microphones in mobile devices also brings the risk of eavesdropping from various attackers, how to design a trustworthy eavesdropping detection technique to identify all eavesdropping attacks?
The electromagnetic radiation (EM) side-channel provides new solutions to the above problems.
- The EM signal generated by the CPU in the mobile device can be used for wireless communication data embedding, so there is a risk of leaking confidential data even on the air-gapped mobile devices.
- Mobile devices generate different EM signals when performing different application tasks, and a reasonable analysis of EM signals can be a breakthrough to identify application usage behavior.
- When an eavesdropping attacker accesses camera/microphone data, the related hardware module also generates EM signals, and capturing such EM signals can be used to achieve the identification of camera/microphone working status.
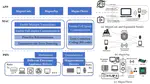
Therefore, this project uses the EM signals generated when the mobile device is running as a side-channel and proposes solutions to three key problems.
- We propose the MagneComm system, which utilizes the EM signal generated by the CPU in the mobile device to embed the data stream and the magnetometer to capture the magnetic field signal for the decoding of the transmitted data. MagneComm system can support a communication distance of 10 cm, and can achieve an effective transmission rate of 110 bps in normal speed communication mode and up to 17.28 kbps in full speed communication mode.
- We conclude from a detailed analysis that the EM signals leaked by mobile devices while executing app tasks are in strong correspondence with the sequence of instruction codes executed by the CPU, and proposes the MagThief system based on this key observation to implement a mobile app usage behavior recognition system that does not require user privileges. MagThief can identify app launch process with 98.6% average accuracy, video content with 98.6% average accuracy, and 90.4% average accuracy of visit websites; MagThief can also achieve 0.87 and 0.95 average F1 macro scores in recognizing multiple apps and in-app services at the same time, respectively.
- We propose a camera/microphone eavesdropping detection system based on EM bypass signals, called MagDefender, by exploiting the physical phenomenon that the device’s on-board hardware module inevitably leaks EM signals when an eavesdropper accesses microphone and/or camera data. MagDefender system is highly accurate and robust in identifying camera/microphone operating states, obtaining an average accuracy of up to 97.3% on trained mobile devices and 91.5% on untrained mobile devices. Compared with existing monitoring methods, the MagDefender system is OS-independent and can detect eavesdropping from advanced attackers (e.g., smartphone vendors).